
Should we be letting flies eat our food waste?
MaryLou Costa Technology Reporter Reporting fromVilnius, Lithuania Energesman Fly larvae are excellent at converting food…











11. Keeping our platforms safe. Our Trust & Safety teams use AI to help detect and flag content that may violate our policies. This saves our teams significant time — a critical advantage when our teams manually reviewed more than one billion pieces of content in 2024 alone. 12. Understanding employee feedback. NotebookLM also helps…

Zoë Schiffer: Right. I love how you said that. Yeah, basically, if you want to potentially try and curry favor with Trump, you buy into one of these schemes, and maybe you’ll get invited to a fancy crypto dinner, which has happened before. Maybe you get something else. But even just the optics here are…

Sophia Allsopp BBC News, West of England BBC The former Debenhams in Gloucester has been transformed into a university building An art charity has said it is “absolutely buzzing” to be part of a £75m city centre university campus that officially opened its doors on Monday. Art Shape, which works with the NHS to deliver…

On March 28, 2025, a magnitude 7.7 earthquake struck the Southeast Asia country of Myanmar along the Sagaing Fault, killing thousands and causing widespread damage. A new study from Caltech uses satellite imaging of the Sagaing Fault’s motion to improve models of how such faults may behave in the future. The study indicates that strike-slip…

Three nano glass spheres cling to one another. They form a tower-like cluster, similar to when you pile three scoops of ice cream on top of one another – only much smaller. The diameter of the nano cluster is ten times smaller than that of a human hair. With the help of an optical device…

/* * Exploit Title : Tenda AC20 16.03.08.12 – Command Injection * Author : Byte Reaper * CVE : CVE-2025-9090 * Description: A vulnerability was identified in Tenda AC20 16.03.08.12. Affected is the function websFormDefine of the file /goform/telnet of the component Telnet Service. * target endpoint : /goform/telnet * place in service :…
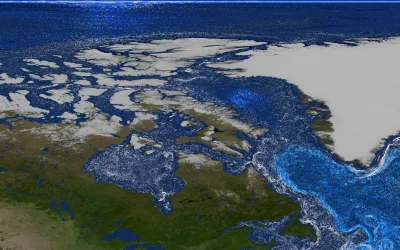
As Greenland’s ice retreats, it’s fueling tiny ocean organisms. To test why, scientists turned to a computer model out of JPL and MIT that’s been called a laboratory in itself. Runoff from Greenland’s ice sheet is kicking nutrients up from the ocean depths and boosting phytoplankton growth, a new NASA-supported study has found. Reporting in…

# Exploit Title: Soosyze CMS 2.0 – Brute Force Login # Google Dork: N/A # Date: 2025-08-13 # Exploit Author: Beatriz Fresno Naumova (beafn28) # Vendor Homepage: https://soosyze.com/ # Software Link: https://github.com/soosyze/soosyze # Version: 2.0 (tested) # Tested on: macOS Sonoma 14.x (Apple Silicon M1), /bin/bash 3.2 & Homebrew bash 5.2, curl 8.x, BSD sed …
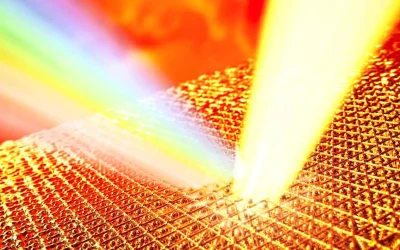
Researchers taking the first-ever direct measurement of atom temperature in extremely hot materials inadvertently disproved a decades-old theory and upended our understanding of superheating. It’s notoriously difficult to take the temperature of really hot things. Whether it’s the roiling plasma in our Sun, the extreme conditions at the core of planets or the crushing forces…

# Exploit Title: Microsoft Windows 10.0.19045 – NTLMv2 Hash Disclosure # Date: 13/08/2025 # Exploit Author: Ruben Enkaoua # Author link: https://x.com/RubenLabs, https://github.com/rubenformation # Original Blog: https://cymulate.com/blog/zero-click-one-ntlm-microsoft-security-patch-bypass-cve-2025-50154/ # Vendor Homepage: https://microsoft.com # Software Link: https://www.microsoft.com/en-us/software-download # Version: All versions prior to patch tuesday august 2025 # Tested on: Windows 10.0.19045 # CVE : CVE-2025-50154 #…